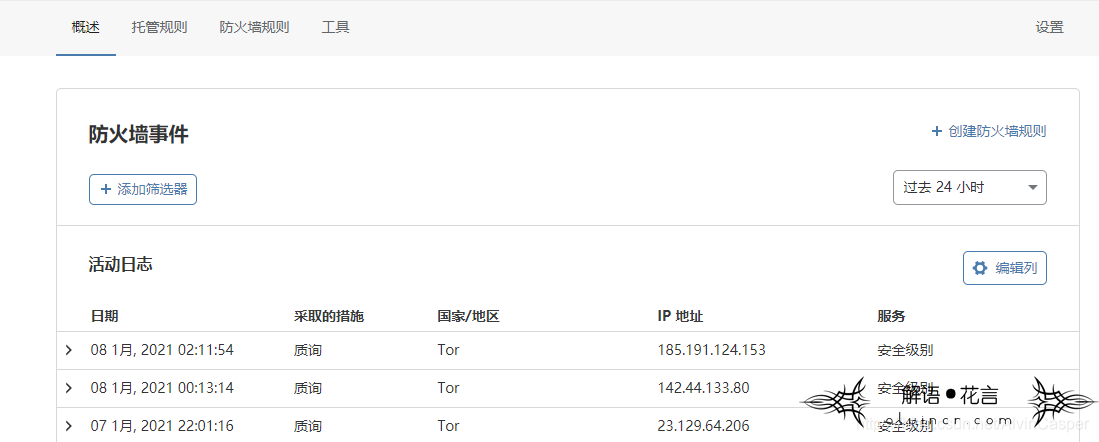
cc attack and countermeasures against attack
view my personal blog original article for more:
1 Basic knowledge
1 What is cc attack
CC attack (Challenge Collapsar Attack, CC) is an attack against web servers or applications, using standard GET/POST requests to obtain information, such as requesting URI (Universal Resource Identifier) involving database operations or other URIs that consume system resources The server resources are exhausted and cannot respond to normal requests.
You can also imitate a cc attack manually by doing this: open a website, hold down ctrl and keep clicking on a webpage link. When the number of links you click in a short period of time exceeds the limit allowed by the server, your visit becomes a cc attack At this time, your IP will be banned for a period of time, and the more ruthless website can directly block your IP.
For example, because I clicked on my site too many times (editing articles), I banned myself, which is commonly known as ruthless, even hitting myself…
2 DDOS attack and cc attack
DDoS attacks hit the server of the website, while the CC attack is aimed at the page of the website. In terms, one is a WEB network layer denial of service attack (DDoS) and the other is a WEB application layer denial of service attack (CC). CC attacks simulate users attacking some web pages that consume more resources, while DDoS attacks target ip. The harms of the two are also different. DDoS attacks are more difficult to defend than CC attacks and cause greater harm.
In summary, DDoS attacks will crash all the websites on your specific server, while cc attacks will only make a lot of visits to specific websites.
In addition: cc is attacking the web page, the server can be pinged, but the web page cannot be accessed.
3 Attack methods
It is divided into broiler cc attack and proxy cc attack. Broiler cc uses many innocent but controlled computers to attack the website (for example, alvincr accidentally opened a virus, and the hacker used my computer to attack alvincr. com)
Broiler CC attack is that hackers use CC attack software to control a large number of broilers and launch an attack. Compared with the latter, it is more difficult to defend than the former. Because the broiler can simulate the request of normal users to visit the website.
Acting CC attack is hacker With a proxy server to generate a legitimate page requests to the victim host, to achieve DDoS, and disguise it called : CC
2 Solution
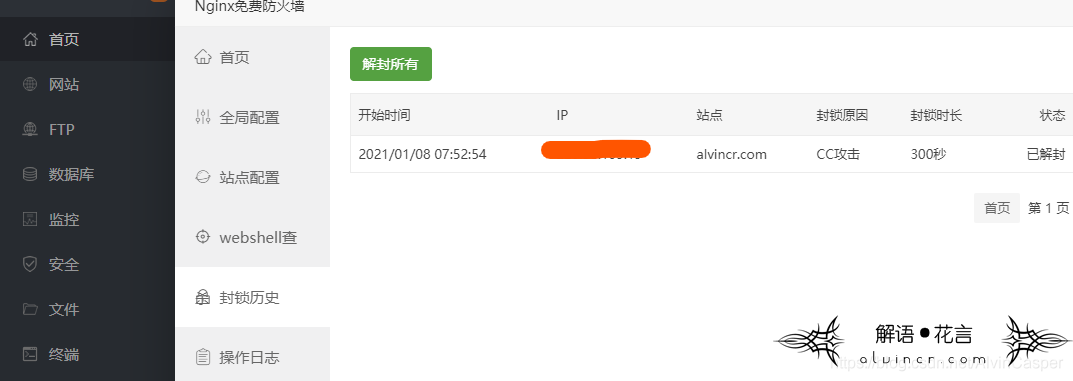
Method 1: Set up a blacklist
If you use the pagoda for management, use the nginx firewall to add a blacklist, or you can add a whitelist so that the situation above will not appear.
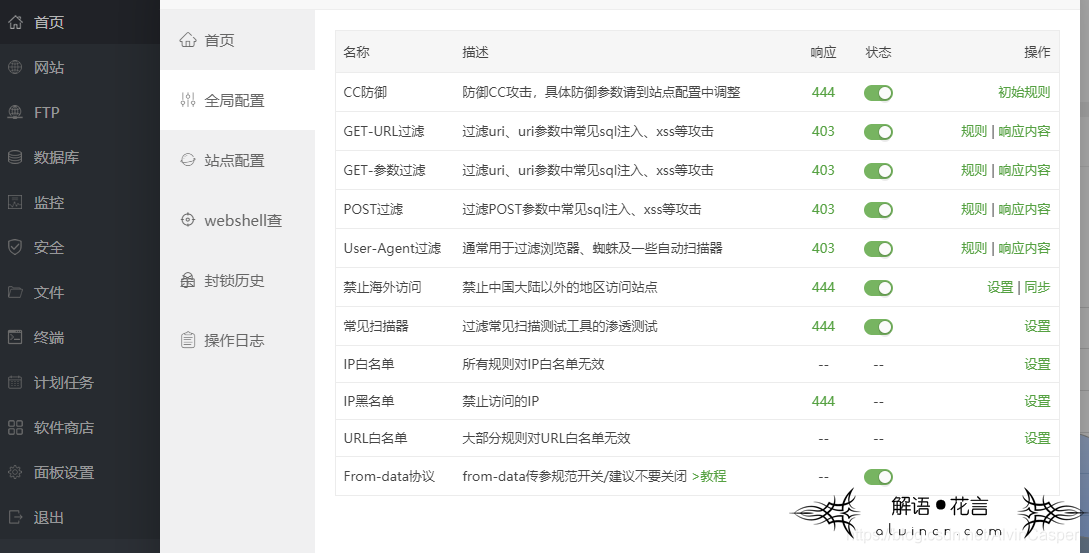
Method 2: nginx’s limit_req_module module
The following is reproduced from (personally think that the following is a machine translation, not the original author): https://www.jianshu.com/p/dff5a0d537d8, the links provided inside are invalid, jump to GitHub can not be accessed, it should be the original author closed the account Up.
http {
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s;
server {
#Limit no more than 20 requests per ip per second, the number of leaky buckets burst is 5
#brust means that if there are 19 requests for the first second, second, third, and fourth second,
#The 5th second request is 25 is allowed.
#But if you have 25 requests in the first second, the requests that exceed 20 in the second second will return a 503 error.
#nodelay, if this option is not set, the average rate is strictly used to limit the number of requests,
#1st second when there are 25 requests, 5 requests will be executed in the second second,
#Set nodelay, 25 requests will be executed in the first second.
limit_req zone=one burst=1 nodelay;
}
}
What does the configuration of the above sample mean?
$binary_remote_addr means: client IP address
zone represents the name of the leaky bucket
rate indicates how fast nginx processes the request
burst means peak
nodelay indicates whether to delay processing the request, or directly return 503 to the client, if the rate setting is exceeded.
For details, please refer to the official documentation: Module ngx_http_limit_req_module
Here we need a small tool like Apache Benchmark to generate requests
//1 user sends a request to the server for 100s
ab -t 100 -c 1 -vvv http://example.com/
Nginx configuration sample one
http {
limit_req_zone $binary_remote_addr zone=one:10m rate=1r/s;
server {
limit_req zone=one burst=1 nodelay;
}
}
Method 3: Enable CDN acceleration
Using CDN acceleration can use the server of the CDN acceleration service provider to automatically block, which saves a lot of worry, but if you are learning web-related knowledge, it is better not to use the blocking of CDN manufacturers. It is better to suffer more attacks and find countermeasures.
Another benefit is: CDN acceleration can cache your web pages, even if your site is abnormal, other people can still see the content of your site.